DDoS attacks are becoming more vicious and the number of occurrences is increasing every day. It’s also starting to become a major headache for small/medium-size businesses as well, we even wrote an article about this.
It’s now extremely difficult to sleep well with just one single DDoS protection service for your website, at least we couldn’t. Many people asked us: “is there any DDoS service out there that can block out attacks entirely without any leakage?” The answer is: no.
As a platform that provides Multi CDN along with security features, we are well aware of this. So when we were designing the platform, we’ve implemented different measures to assure our users’ websites are protected when being accessed via the CDNs.
What happens when an attack occurs
With all requests passing through Mlytics Multi CDN, managing traffic and protect against malicious requests is really simple via port restriction.
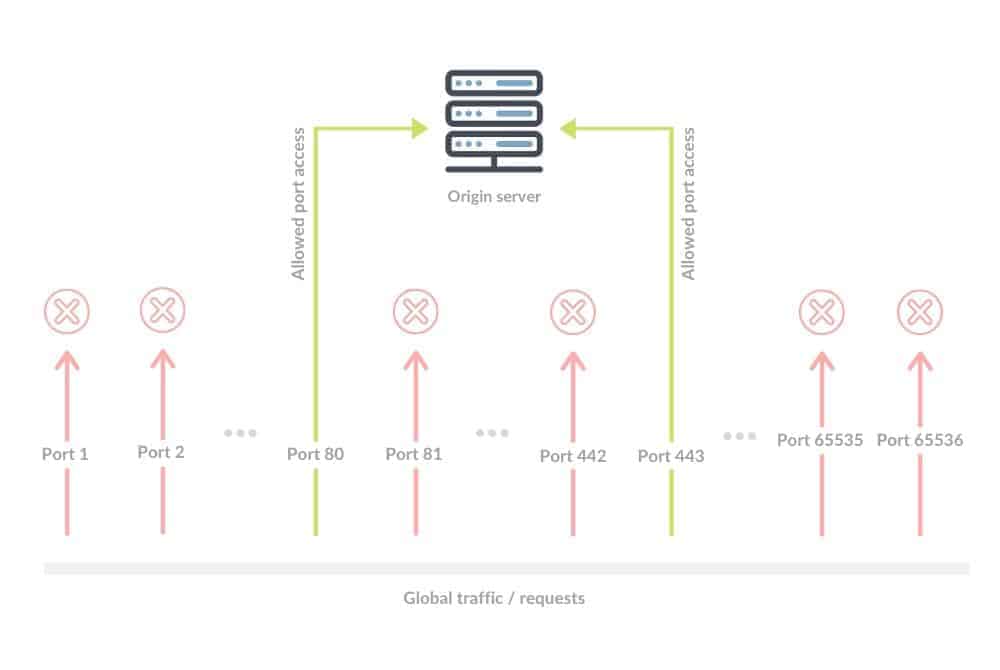
When an attack happens, all malicious requests targeting L3/L4 that aren’t accessing via port 80 and 443 will be filtered out automatically for users due to the fact that CDNs strictly only allow port 80 and 443 accesses. Even if there are port 80 or 443 malicious requests, the bandwidth which Multi CDN provides is large enough to absorb most of the attack.
These attacks are being absorbed (or scrubbed) locally at the source of the attack via the edge server (CDN) instead of potentially redirecting it to a scrubbing center that’s thousands of miles away. This is called the “local scrubbing” method.
Most L3/L4 attacks can be mitigated here.
As for L7 attacks, aiming to provide consistent security policies and overall security quality across all CDNs, Mlytics does not use any third-party DDoS protection services and have disabled all the default CDN DDoS features. Instead, Mlytics uses its own advanced DDoS protection technology to unify the security policy and keep users’ origin server protected from all L7 attacks.
Protecting the core: L7 protection
We offer multiple L7 DDoS attack mitigation methods, including block scanner, block crawlers, browser integrity check, and challenge & response. Most application layer attacks can be mitigated automatically by default. But some still find the remaining attacks overwhelming, thus these features serve as a powerful tool for our users to take different measures depending on types of incoming L7 attacks.
We have data centers in multiple locations including Ireland, Los Angeles, Taiwan, Hong Kong, and more globally to host our DDoS protection services and WAF. This allows us to fight attacks while not having to worry about sacrificing performances.
WAF, an extra layer of safety net
While different from the DDoS protection services, our self-developed WAF can serve as a powerful ally to the Mlytics DDoS protection eco-system.
It’s no news that Mlytics has its own WAF, we’ve also written an article about why and how we developed our own web application firewall.
We are actively monitoring what’s going on on the internet and getting security insights way before everyone else. This information allows us to proactively patch our users’ domain if there is any vulnerability via our web application firewall.
We can even patch vulnerabilities that are found in the CDN from the Multi CDN lineup which we provide. A good example was we patched Cloudflare’s bypass vulnerability back in January 2019. You can read all about it here.
The Mlytics WAF is continuously evolving as we are in the driver seat to enhance it (or patch it) whatever and whenever we want, giving our users extra protection when comparing to the vanilla WAF that’s available on the market.
A layered DDoS protection process
Some said Mlytics doesn’t have its own DDoS protection mechanism and we are using third-party DDoS protection services as our main DDoS mitigation measure, this is simply not true. To sum it up, we have a layered DDoS protection process to keep users protected:
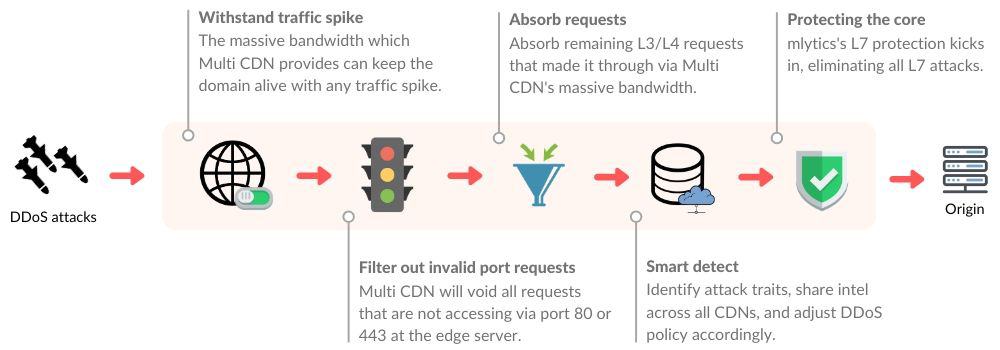
- We use port restriction via Multi CDN to void all requests that are not accessing via port 80 or 443
- The Multi CDN’s combined total of 2,300+ PoPs and 2,600 Tbps capacity can easily absorb (scrub) all of the L3/L4 attacks at the source if there are port 80 or 443 attacks
- Mlytics L7 protection will focus on protecting the origin server from all L7 attacks